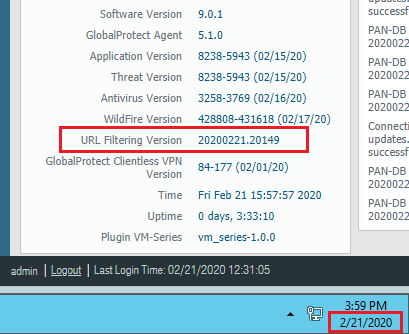
Palo Alto URL Filtering category. What are the Palo Alto Networks test URLs for the real-time-detection category.
Palo Alto Networks NGFWs with cloud-delivered security services like URL Filtering WildFire and Threat Prevention provide comprehensive visibility and granular policy control enhancing security protections across all form factors.
Palo alto url categories. PAN-DB classifies websites based on site content features and safety. A URL can have up to four categories including risk categories high medium and low which indicate how likely it is that the site will expose you to threats. For a complete list of predefined URL.
PAN-DB classifies websites based on site content features and safety. A URL can have up to four categories including risk categories high medium and low which indicate how likely it is that the site will expose you to threats. For a complete list of predefined URL.
You can create a custom URL category to define exceptions to URL category policy enforcement or build a distinct category from existing PAN-DB categories. You can create a custom URL filtering object to specify exceptions to URL category enforcement and to create a. The firewall classifies sites known to host malware credential phishing pages and other risky content as any of the following malicious URL categories.
We strongly recommend that you block the URL categories that identify malicious or exploitive content. To get started you can clone the default URL Filtering profile which blocks malware. If there is a specific site that you would like to determine the URL category please visit this site to test the URL.
The following is a complete list of PAN-DB URL filtering categories. For PAN-OS 41 and 50 go to Objects Custom URL Category and click Add. For PAN-OS 60 and 61 Custom URL Category has been renamed as URL Category and moved under Objects Custom Objects.
Fill in the Name Description and. Palo Alto Networks URL filtering - Test A Site. Did you know that PAN-DB the Palo Alto Networks URL database can assign multiple categories to URLs that classify a websites content purpose and safety.
Every URL can have up to four categories including a security-focused URL category that indicates how likely it is that the site will expose you to threats. Hi is it possible to list all available url-categories via CLI on palo alto firewall. Show predefined url-categories is not the right thing it shows some url-categories but most of them are not valid Eg hobbies-and-recreation should actually be recreation-and-hobbies.
Palo Alto Firewalls. PAN-OS 61 and above. The Maximum limit of Custom URL Categories is listed below per Pan-OS version All hardware have the same limit.
Starting from PAN-OS 81 the above Limit is Per VSYS and the Maximum Limit of Custom Categories is 2048 per Firewall. The URLs are as follows. BrightClouds URL Test Site.
Palo Alto Networks URL Test site. URL categorization can still be verified from the CLI with the following command below. What are the Palo Alto Networks test URLs for the real-time-detection category.
You can use the following test domains to test real-time-detection categories. These testing URLs are 100 benign and have been categorized to their respective categories for testing purposes. First after logging into your Palo Alto Networks Next-Generation Firewall click the Policies tab.
Then in the list of options on the left click Security. A URL Category column will appear Figure 1. URL Category in the security policy.
If you do not see the URL Category column on your interface it is most. In addition to the standard URL categories there are three additional categories. URL Filtering Profile Actions.
Block Block page displayed to the user Continue. Block and allow lists. URL filtering response pages.
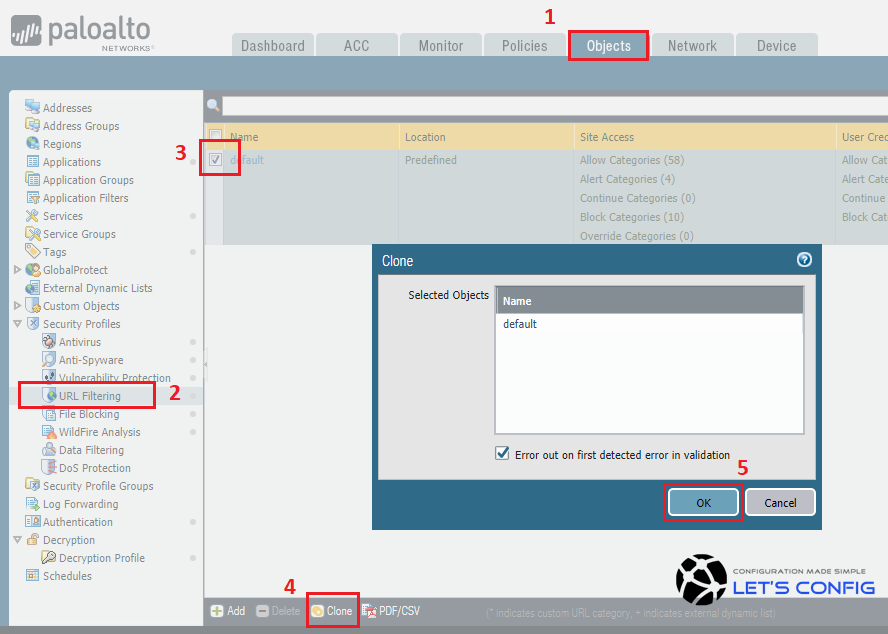
Block Block page displayed to the user. The default URL Filtering profile in Palo Alto blocks the abused-drugs adult command-and-control gambling grayware hacking malware phishing questionable and weapons URL categories. Now select the default 3 profile and click Clone 4 and then click OK 5.
Custom URL Categories. Objects Custom URL Categories. The custom URL categories feature allows you to create your own lists of URLs that can be selected in any URL filtering profile.
Each custom category can be controlled independently and will have an action associated with it in each URL filtering profile allow block continue override. Palo Alto URL Filtering category. Palo Alto Networks have added a new URL filtering category called command-and-control to identify the differences between malware and command and control c2 URLs and domains.
Until the new category is live the URLs and domains are recorded with the malware category. To do so use the following resources. Virus Total and Palo Alto URL Test Page.
If the webpage is listed by Palo Alto as one of the categories blocked by the UW-Madison profile in use. Malware phishing or command and control but the webpage is known trusted to be legitimate and comes back with a low score on VirusTotal the Palo Alto test page has the option to request a re. On the Palo Alto Networks firewall create a new URL Filtering profile.
Select Objects Security Profiles URL Filtering. Select the default profile and then click Clone. The new profile will be named default-1.
Select the default-1 profile and rename it. For example rename it to URL-Monitoring. Configure the action for all categories to alert.
Palo Alto Networks NGFWs with cloud-delivered security services like URL Filtering WildFire and Threat Prevention provide comprehensive visibility and granular policy control enhancing security protections across all form factors. Palo Alto Networks researchers maintain full coverage for all command-and-control traffic observed inWildFire. These signatures provide a key method for identifying and controlling any malware infections already in the network.
WildFire monitors any URLs and domains that. Per the Palo Alto Networks instructions its straightforward. Select or create a new URL filter.
Under the Categories select Alert for Newly Registered Domain. Note Alert will not block the access. It is required to Syslog out to the SIEM.
Block will not only block access to the URL but it will also log it to the SIEM.